
00107 Cybersecurity in Medical Devices- Documentation Supporting Software Bill of Materials
Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions
(b) Documentation Supporting Software Bill of Materials454
455
FDA’s guidance documents “Off-The-Shelf (OTS) Software Use in Medical Devices”30 and456
“Cybersecurity for Networked Medical Devices Containing Off-the-Shelf (OTS) Software”31
457
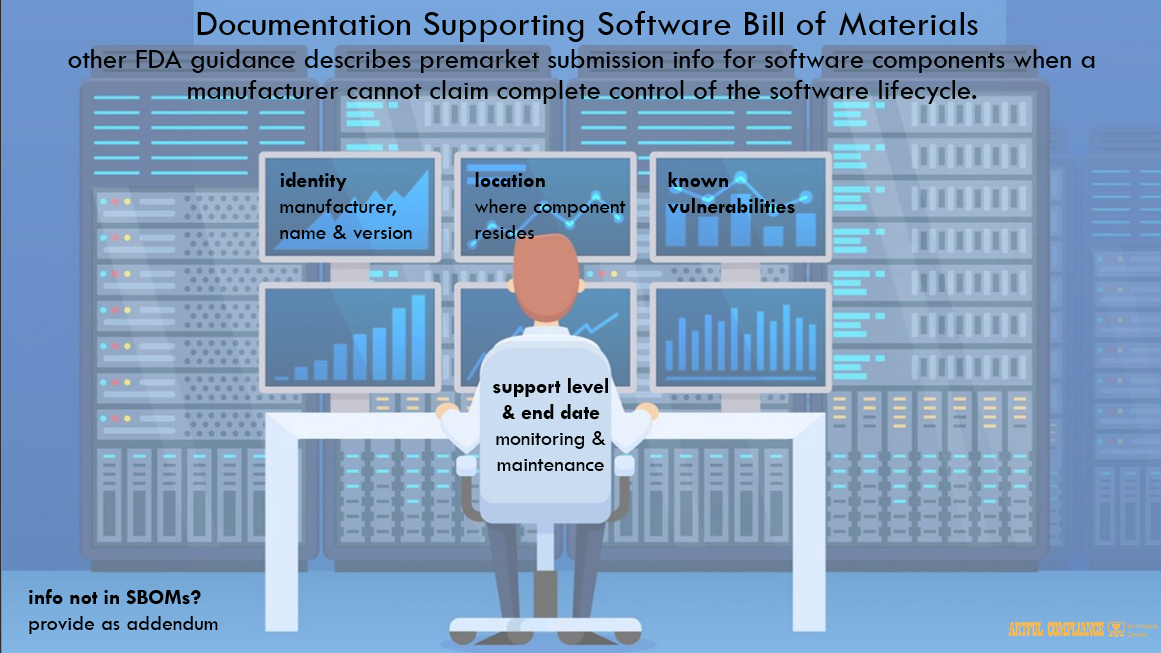
describe information that should be provided in premarket submissions for software components458
for which a manufacturer cannot claim complete control of the software lifecycle. In addition to459
the information recommended in those guidances, for each OTS component, the following460
should also be provided in a machine-readable format in premarket submissions.461
462
A. The asset(s) where the software component resides;463
B. The software component name;464
C. The software component version;465
D. The software component manufacturer;466
E. The software level of support provided through monitoring and maintenance from467
the software component manufacturer;468
F. The software component’s end-of-support date; and469
G. Any known vulnerabilities.32
470
471
Industry-accepted formats of SBOMs can be used to provide this information to FDA; however,472
if any of the above elements are not captured in such an SBOM, we recommend that those items473
also be provided, typically as an addendum, to FDA for the purposes of supporting premarket474
submission review. Additional examples of the type of information to include in a SBOM can be475
found in the Joint Security Plan – Appendix G (“Example Customer Security Documentation”)33
476
and Sections 2.3.17 and 2.3.18 of the Manufacturer Disclosure Statement for Medical Device477
Security (referred to as MDS2 or MDS2)34.478
479
As part of the premarket submission, manufacturers should also describe how the known480
vulnerabilities (item (G) above) were discovered to demonstrate whether the assessment methods
ere sufficiently robust. For third-party components with known vulnerabilities, device482
manufacturers should provide in premarket submissions:483
484
· A safety and security risk assessment of each known vulnerability; and485
· Details of applicable safety and security risk controls to address the vulnerability. If risk486
controls include compensating controls, those should be described in an appropriate level487
of detail488
489
For additional information and discussion regarding proprietary and third-party components, see490
section V.B.2., Security Architecture Views, below
Recent Comments