
00105 Cybersecurity in Medical Devices- 3rd Party Software Components
Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions
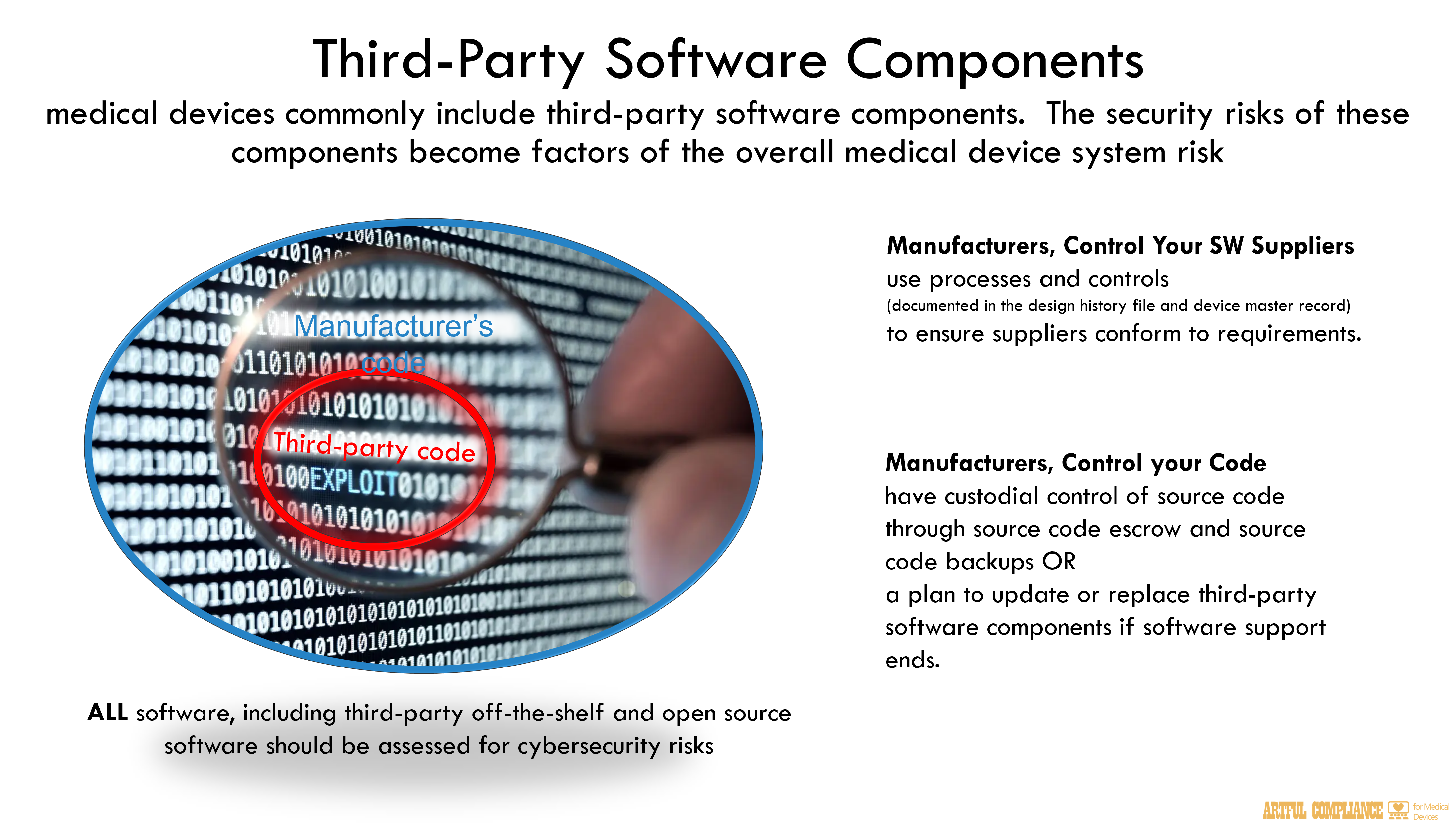
- Third-Party Software Components
As discussed in the FDA guidances “Off-The-Shelf (OTS) Software Use in Medical Devices”
and “Cybersecurity for Networked Medical Devices Containing Off-the-Shelf (OTS) Software,”26 medical devices commonly include third-party software components including off-the-shelf and open source software. When these components are incorporated, security risks of the software components become factors of the overall medical device system risk management processes and documentation.
As part of demonstrating compliance with quality system design controls under 21 CFR 820.30(g), and to support supply chain risk management processes, all software, including that developed by the device manufacturer (“proprietary software”) and obtained from third parties should be assessed for cybersecurity risk and that risk should be addressed. Accordingly, device manufacturers are expected to document all software components27 of a device and to mitigate risks associated with these software components.408
409
In addition, under 21 CFR 820.50, manufacturers must put in place processes and controls to410
ensure that their suppliers conform to the manufacturer’s requirements. Such information is411
documented in the Design History File, required by 21 CFR 820.30(j), and Design Master412
Record, required by 21 CFR 820.181. This documentation demonstrates the device’s overall413
compliance with the QSR, as well as that the third-party components meet specifications414
established for the device. Security risk assessments that include analyses and considerations of415
cybersecurity risks that may exist in or be introduced by third-party software and the software416
supply chain may help demonstrate that manufacturers have adequately ensured such417
compliance and documented such history.418
419
As part of configuration management, device manufacturers should have custodial control of420
source code through source code escrow and source code backups.28 While source code is not421
provided in premarket submissions, if this control is not available based on the terms in supplier422
agreements, the manufacturer should include in premarket submissions a plan of how the third-423
party software component could be updated or replaced should support for the software end. The424
device manufacturer is also expected to provide to users whatever information is necessary to425
allow users to manage risks associated with the device.426
427
One tool to help manage supply chain risk as well as clearly identify and track the software428
incorporated into a device is a Software Bill of Materials (SBOM), as described below
Recent Comments