
00104 Cybersecurity in Medical Devices- Threat Modeling
Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions
1.Threat Modeling357
358
Threat modeling includes a process for identifying security objectives, risks, and359
vulnerabilities across the system, and then defining countermeasures to prevent, or mitigate the360
effects of, threats to the system throughout its lifecycle. It is foundational for optimizing361
system, product, network, application, and connection security when applied appropriately and362
comprehensively.363
364
With respect to security risk management, and in order to identify appropriate security risks365
and controls for the system, FDA recommends that threat modeling be performed to inform366
and support the risk analysis activities. As part of the risk assessment, FDA recommends threat367
modeling be performed throughout the design process and be inclusive of all system elements.
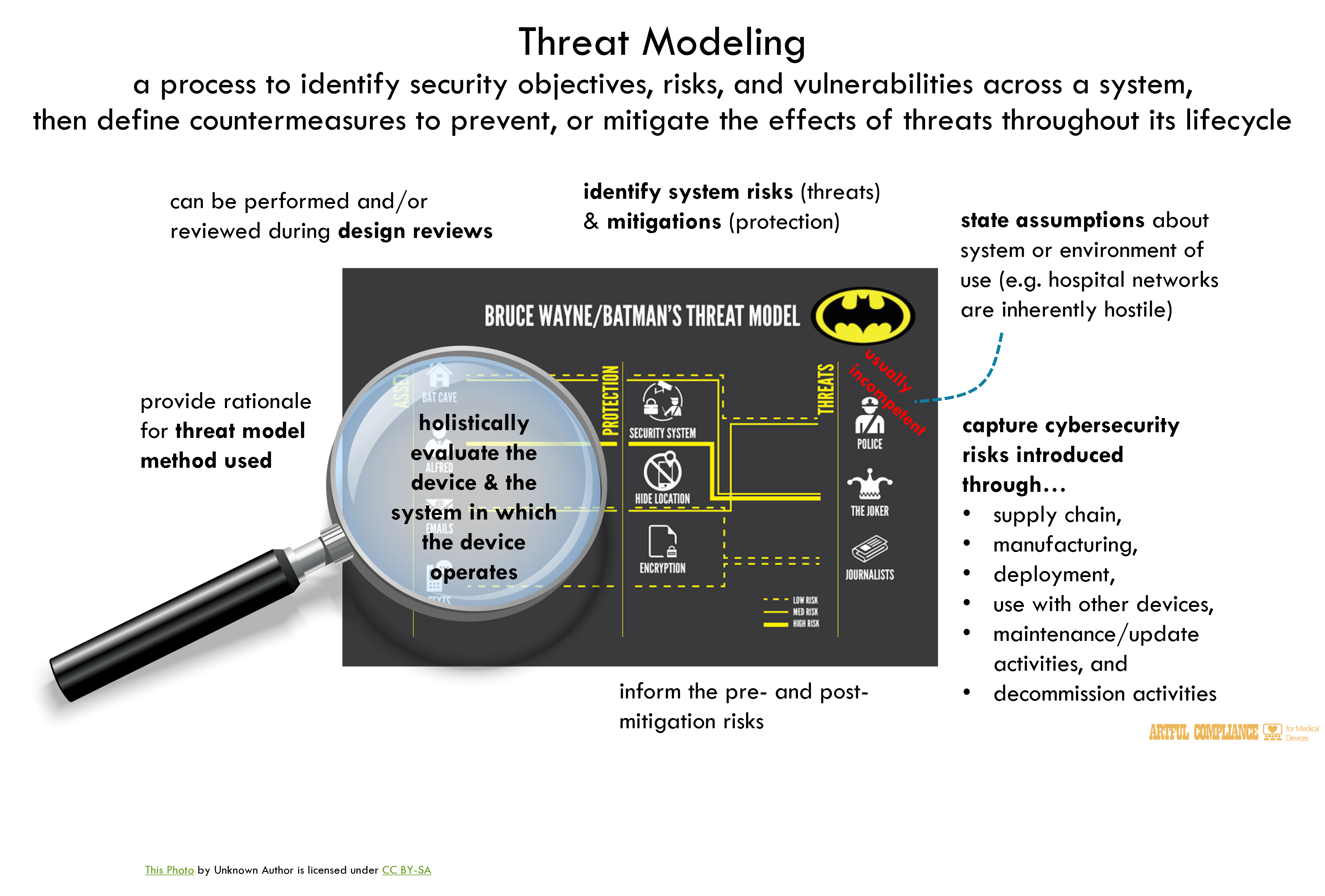
2.he threat model should:370
· identify system risks and mitigations as well as inform the pre- and post-mitigation371
risks considered as part of the security risk assessment;372
· state any assumptions about the system or environment of use (e.g. hospital networks373
are inherently hostile, therefore manufacturers are recommended to assume that an374
adversary controls the network with the ability to alter, drop, and replay packets); and375
· capture cybersecurity risks introduced through the supply chain, manufacturing,376
deployment, interoperation with other devices, maintenance/update activities, and377
decommission activities that might otherwise be overlooked in a traditional safety risk378
assessment processes.379
380
FDA recommends that premarket submissions include threat modeling documentation to381
demonstrate how the risks assessed and controls implemented for the system address questions382
of safety and effectiveness. There are a number of methodologies and/or combinations of383
methods for threat modeling that manufacturers may choose to use. Rationale for the384
methodology(ies) selected should be provided with the threat modeling documentation.385
Additional recommendations on how threat modeling documentation should be submitted to386
FDA are discussed in Section V.B. below.387
388
Threat modeling activities can be performed and/or reviewed during design reviews. FDA389
recommends that threat modeling documentation include sufficient information on threat390
modeling activities performed by the manufacturer to assess and review the security features391
built into the device such that they holistically evaluate the device and the system in which the392
device operates, for the safety and effectiveness of the system.
Recent Comments