
00102 Cybersecurity in Medical Devices- Security Risk Management
Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions
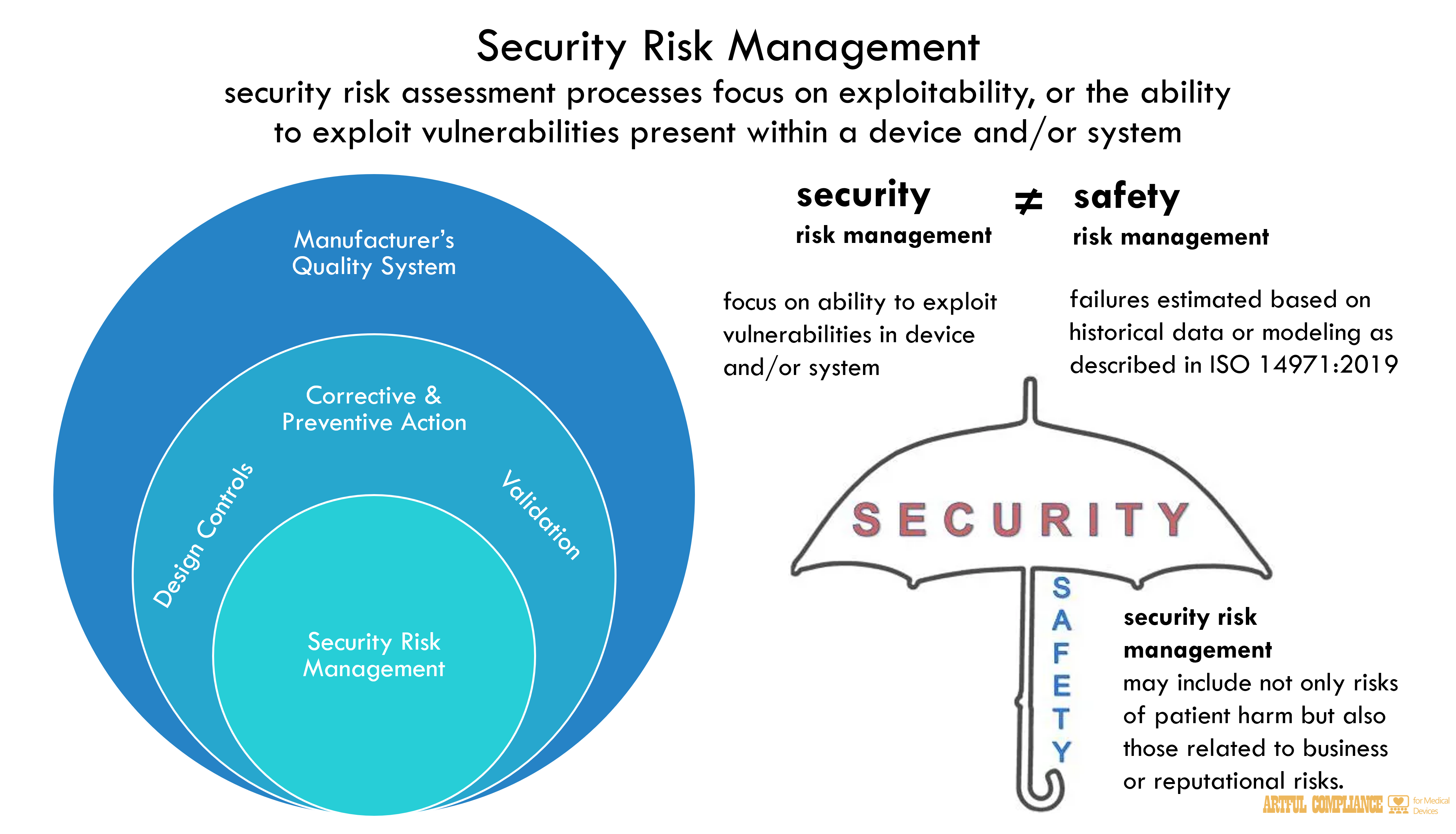
A.Security Risk Management
To fully account for cybersecurity risks in devices, the safety and security risks of each device should be assessed within the context of the larger system in which the device operates. In the context of cybersecurity, security risk management processes are critical because, given the evolving nature of cybersecurity threats and risks, no device is, or can be, completely secure. Security risk management should be part of a manufacturer’s quality system. Specifically, the QSR requires, among other things, that manufacturers’ processes address design (21 CFR298
820.30), validation of the production processes (21 CFR 820.70), and corrective or preventive actions (21 CFR 820.100). These processes entail the technical, personnel, and management practices, among others, that manufacturers use to manage potential risks to their devices and ensure that their devices remain safe and effective, which includes security.302
303
The process for performing security risk management is a distinct process from performing safety risk management as described in ISO 14971:2019. This is due to the scope of possible harm and the risk assessment factors in the context of security may be different than those in the context of safety. Also, while safety risk management focuses on physical injury or damage to property or the environment, security risk management may include not only risks
that can result in patient harm but also those risks that are outside of FDA’s assessment of safety and effectiveness such as those related to business or reputational risks.310
311
Effective security risk management also addresses that cybersecurity-related failures do not occur in a probabilistic manner where an assessment for the likelihood of occurrence for a313
particular risk could be estimated based on historical data or modeling. This non-probabilistic314
approach is not the fundamental approach described in safety risk management under ISO315
14971:2019. Instead, security risk assessment processes focus on exploitability, or the ability316
to exploit vulnerabilities present within a device and/or system. Additional discussion on317
exploitability assessments for the security risk assessment can be found in the FDA’s318
Postmarket Cybersecurity Guidance.22 Exploitability for a cybersecurity risk during a319
premarket assessment may be different compared to a risk assessment performed for a320
postmarket vulnerability. For example, some of the exploitability factors discussed in the321
guidance (e.g., Exploit Code Maturity, Remediation Level, Report Confidence23) may not be322
applicable to unreleased software. In these instances, a premarket exploitability assessment323
could either assume a worst-case assessment and implement appropriate controls, or provide a324
justification for a reasonable exploitability assessment of the risk throughout the total product325
lifecycle and how the risk is controlled.
B.FDA recommends that manufacturers establish a security risk management process that328
encompasses design controls (21 CFR 820.30), validation of production processes (21 CFR329
820.70), and corrective and preventive actions (21 CFR 820.100) to ensure both safety and330
security risks are adequately addressed. For completeness in performing risk analyses under 21331
CFR 820.30(g), FDA recommends that device manufacturers conduct both a safety risk332
assessment per ISO 14971:2019 and a separate, accompanying security risk assessment to333
ensure a more comprehensive identification and management of patient safety risks. The scope334
and objective of a security risk management process, in conjunction with other SPDF processes335
(e.g., security testing), is to expose how threats, through vulnerabilities, can manifest patient336
harm and other potential risks. These processes should also ensure that risk control measures337
for one type of risk assessment do not inadvertently introduce new risks in the other. AAMI338
TIR57:2016 details how the security and safety risk management processes should interface to339
ensure all risks are adequately assessed.24
340
341
Recent Comments